Authentication > Integrate OneLogin
Integrate Google Suite
This guide explains how to set up SAML-based Single Sign-On (SSO) between Google Workspace (formerly G Suite) and Tallyfy to enable automated user authentication and provisioning.
- Google Workspace administrator account with super-administrator privileges
- Tallyfy Professional or Enterprise plan
- SAML configuration values from Tallyfy Support
The integration involves three main phases:
-
Sign in to the Google Workspace Admin console ↗
-
Navigate to Apps > Web and mobile apps
-
Click Add App > Add custom SAML app

- Enter “Tallyfy” as the application name
- Optionally upload the Tallyfy logo
- Click Continue to proceed to the next step
-
On the Google Identity Provider details page, collect the SSO URL (Single Sign-On URL).
-
Collect the Entity ID (Issuer).
-
Download the Certificate file.

-
Enter the Tallyfy ACS URL (Assertion Consumer Service URL) provided by Tallyfy Support.
-
Enter the Tallyfy Entity ID (Service Provider Entity ID) provided by Tallyfy Support.
-
Leave the Start URL field empty.

Map the following user attributes:
| Google Directory Attribute | App Attribute |
|---|---|
| Primary Email | |
| First Name | firstName |
| Last Name | lastName |
Click Finish to complete the application setup.
-
In the application settings, go to User Access
-
Set the Service status to ON for everyone (or select specific organizational units)

- Provide the collected SSO URL to Tallyfy Support.
- Provide the collected Entity ID to Tallyfy Support.
- Provide the downloaded Certificate file to Tallyfy Support.
-
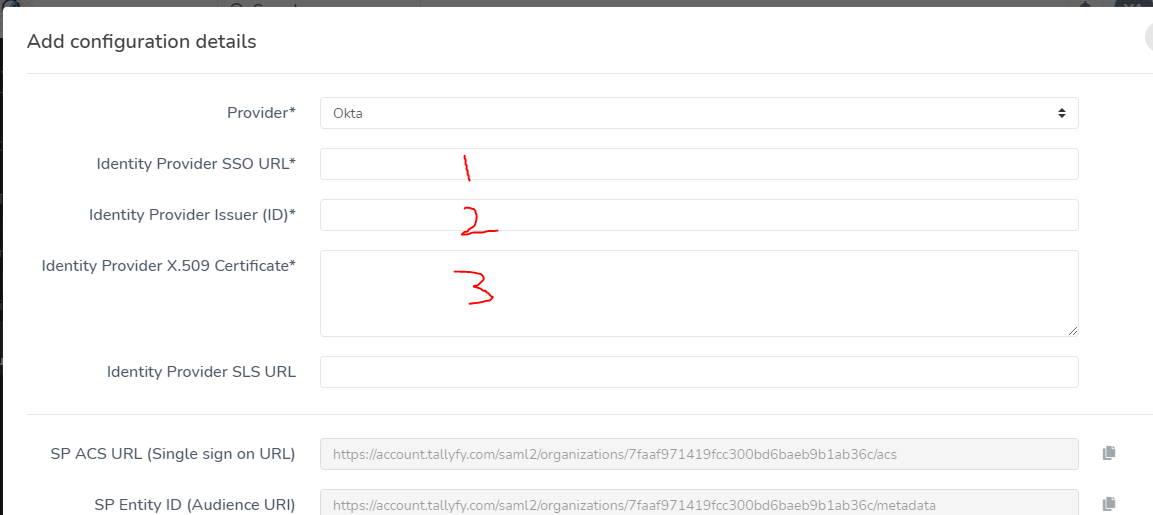
Once Tallyfy Support has processed your information, navigate to your organization settings
-
Locate the SAML configuration section
-
Enter the configuration details as provided by Tallyfy Support
-
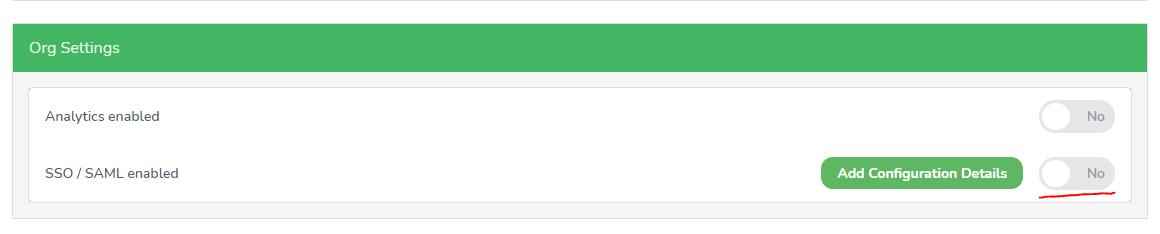
Toggle the SAML activation switch to enable SSO for your organization
Once the integration is complete:
-
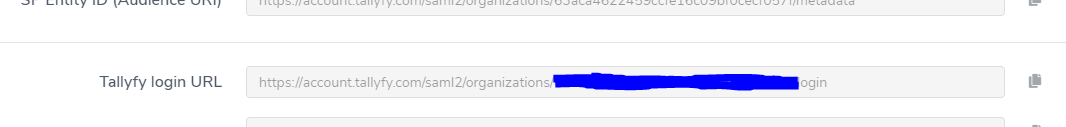
Share the Tallyfy login URL with your users (available in the SAML configuration modal).
-
Ensure users who need access have been granted access to the SAML app in Google Workspace.
-
Existing Tallyfy users can now sign in via the shared SSO URL without requiring separate Tallyfy credentials.
-
New users will be automatically provisioned in Tallyfy upon their first login via the shared SSO URL.
If users encounter authentication issues:
- Verify the user has been granted access to the SAML app in Google Workspace
- Ensure attribute mappings are correctly configured
- Check that the user is accessing Tallyfy through the proper SSO URL
- Contact Tallyfy Support for assistance with persistent issues
Authentication > Integrate Okta
Authentication > Integrate Azure AD
Integrations > Authentication and SSO
- 2025 Tallyfy, Inc.
- Privacy Policy
- Terms of Use
- Report Issue
- Trademarks