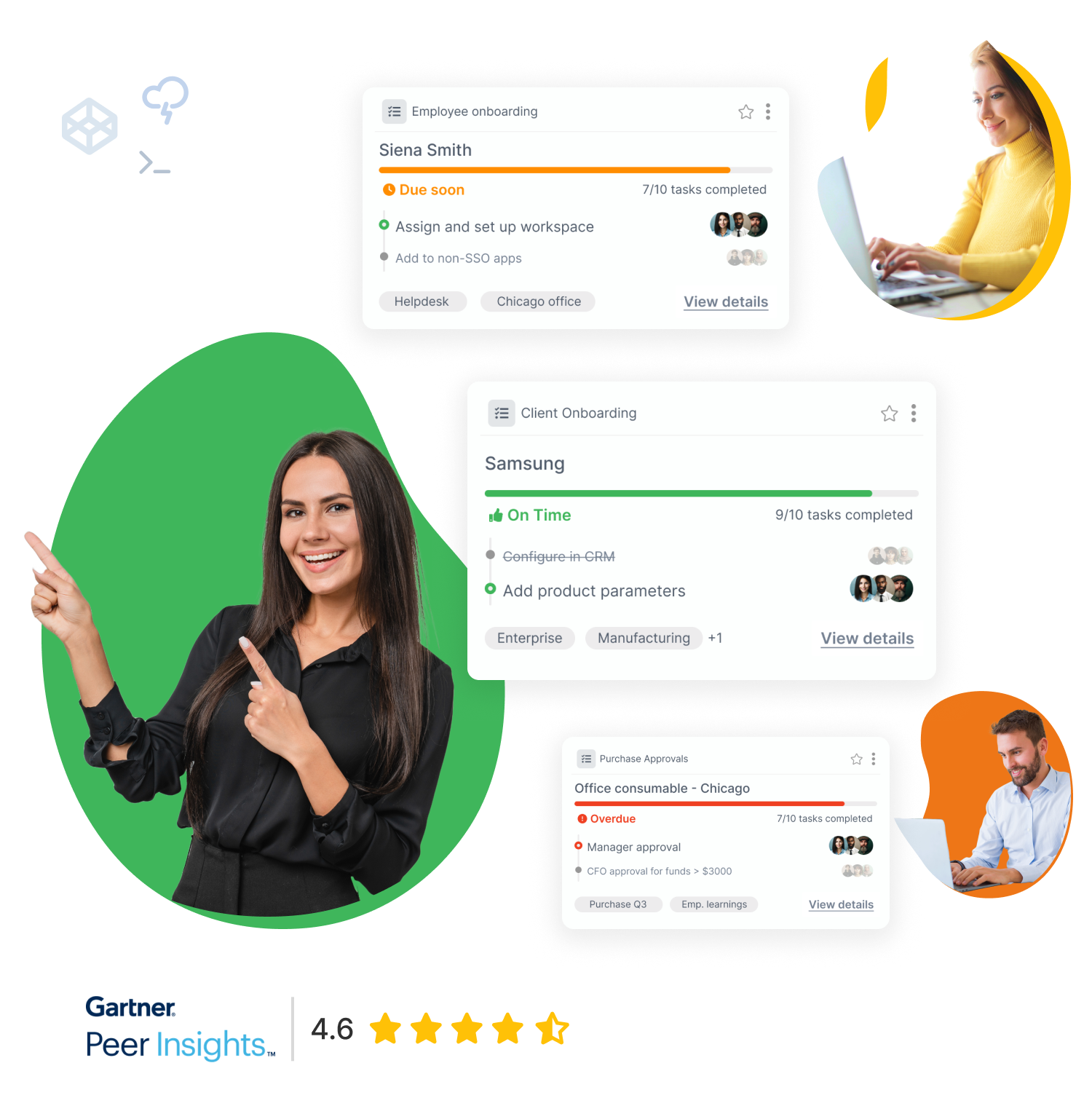
When you own your own business, it’s essential to make sure that it’s secure and free from potential risks. These risks can come from a variety of sources from employees and customers to competitors and cyber attacks. Other risks come when you decide to make investments in new business-related expenses. All of these expenses need to be evaluated for the risks involved to make sure that you’ll come out a winner – which is where risk assessment software comes in.
Last year, IDG detected 38 percent more cybersecurity incidents than the year prior.Bill Laberis
Information security risk assessment software helps your company create a protocol to check for risks in the most sensitive areas where problems might arise. This information risk assessment software provides the means to make periodic checks on your information and other systems to ensure that nothing has changed and that your possible risk hasn’t grown. Keeping your business healthy and growing is your main goal and information risk assessment software can aid you in that effort. Here’s how it works.
Identify Information, Who Controls It, and Who Benefits From It
It’s hard to access the risk to something if you aren’t exactly sure what it is. Information risk assessment software can help you identify the information that is most at risk in your company, and then you can come up with a plan to protect it more easily.
Part of this assessment from your information risk assessment software should identify who is responsible for creating the information and organizing it. These will be the people who make the changes to tighten any security if the information risk assessment software finds an issue.
Another issue in this initial step is to find out who benefits from the information or asset. The information risk assessment software will help to identify all of these things.
What Happens if the Information Were Compromised
The next step in determining the risk to your information and company is to determine what would happen if the information was compromised. The information risk assessment software looks at what the long-term effect would be if the information were to leak to determine how detrimental it would be to the health of your company.
It could be that the information risk assessment software finds that the information isn’t as important to your company as you thought that it was while identifying other items more important. Knowing the long-term effects of a breach of information can help you decide how much you are or aren’t willing to do to protect that information from the current risk. While the information risk assessment software suggests the possible outcome, you won’t know until it actually happens.
Identify Possible Threats By Doing Risk Assessment
You can’t protect something until you have an understanding of what the threats are to it. Information risk assessment software helps to identify those threats. Threats to information at your company can come from within the company or someone outside of it. To get the best idea of the potential threats, use the information risk assessment software as an aid.
It’s possible that your company allows too many employees to access a piece of information placing it at risk. The information risk assessment software might identify a specific group of employees or departments that don’t really need access or who should have limited access to stricter controls. You want to make sure that you use your information risk assessment software to continually identify possible threats to your most essential company information.
Look at Possible Weak Points Within Risk Assessment Software
Once your information risk assessment software has identified areas of concerns, it’s up to your company to take a long hard look at any weak points that the system has identified. Although your information risk assessment software looks at information and figures to make a determination, it’s impossible for the software to see the actual flow.
To keep your company protected and growing, you want to examine the identified areas and check each step of the current process to ensure that the information identified by the information risk assessment software is actually at risk. From there, it’s up to you to make changes to shore up those risks.
While investigating the weak points, you want to try and determine the likelihood that the person or group identified by the information risk assessment software could actually access the information. It’s possible that the information risk assessment software sees a possibility that isn’t really practical in reality.
Examine the Controls That Protect the Information
When the information risk assessment software identifies a possible weak point, it also needs to examine the controls that you already have in place to protect that information. This can include items, such as who has access to the items, how you determine if someone who doesn’t have access has seen the information and any encryption in place.
The information risk assessment software examines the types of protocol that you have in place for weaknesses in the controls. You might need to add additional controls to further protect your company’s essential information. With information risk assessment software, you can get a real assessment of whether or not your current controls are enough to protect your company secrets. Once you’ve implemented new controls, you’ll need your information risk assessment software to examine the new controls in the same manner.
Is the Threat Real?
After the information risk assessment software identifies the threat and examines the controls in place, it’s time for your company to decide if the threat is real. At this point, you can benefit from creating pretend scenarios. You can select a possible threat and pretend like it’s trying to access your information. You need to carefully examine what roadblocks stand in the person’s way and if they are enough to block them from accessing it.
Your information risk assessment software helps you work out these scenarios. It’s essential that your company is making changes only when the possibility of a problem is real. You don’t want to waste money and resources if the threat is highly unlikely of ever occurring.
Determine the Residual Risk
After your information risk assessment software finds a weak area, you need to determine exactly how bad it would be if that information were compromised. You need to take a look at the long-term effects if a piece of information was known to the outside world. In some cases, information might not be as essential as time goes by.
For instance, you might need to heavily guard information about an upcoming new product line, but once the line is launched, you don’t need to protect it as much or even at all. Your information risk assessment software can help you decide where to add additional barriers as well as when it’s no longer essential.